This CTF is part of the SOC Level 1 learning path on TryHackMe. You are tasked to investigate a compromised corporate system using limited Splunk logs.
You can find the link to Benign here.
Overview#
In this scenario, we were only able to pull the process execution logs with
Event ID: 4688 into Splunk, so we don’t have access to all Sysmon logs.
We’re also told the network is divided into 3 segments:
IT Department
- James
- Moin
- Katrina
HR Department
- Haroon
- Chris
- Diana
Marketing Department
- Bell
- Amelia
- Deepak
With these helpful facts in mind, let’s start!
Questions#
How many logs are ingested from the month of March, 2022?#
This is easy to figure out as we can set the date range to be within March 2022, and query the given index:
index=win_eventlogs
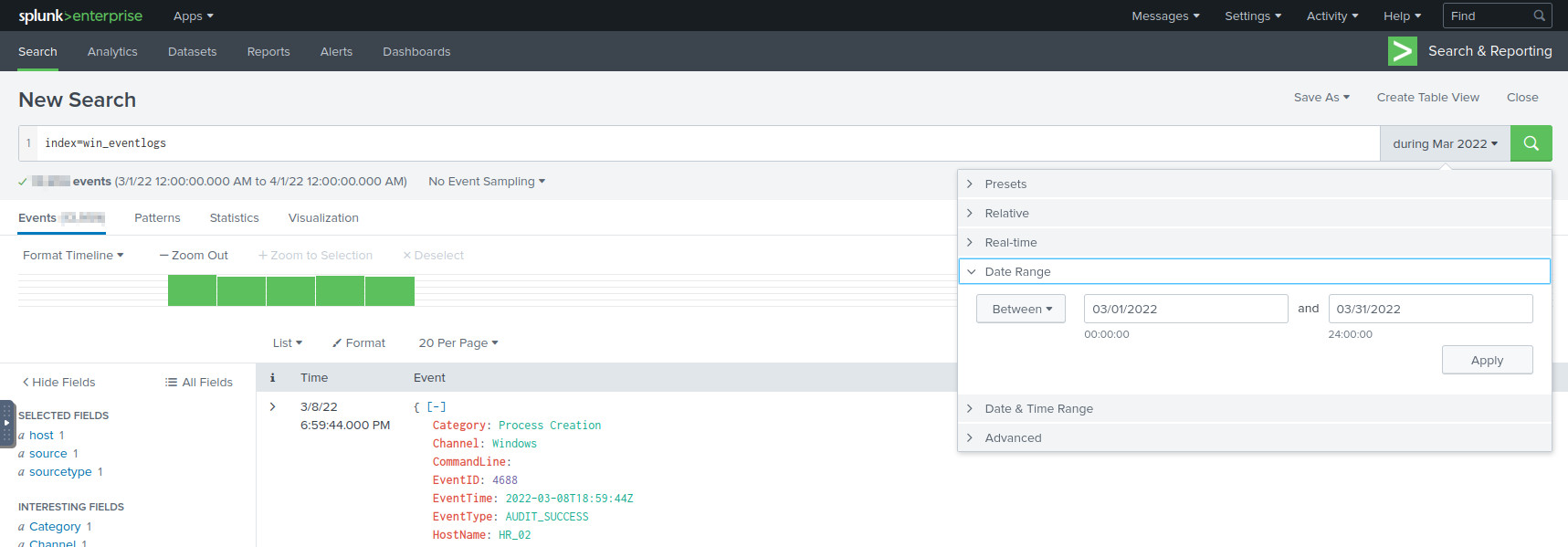
Setting the date range in Splunk.
Imposter Alert: There seems to be an imposter account observed in the logs, what is the name of that user?#
There’s a UserName field, so we can create a table to list all of the
users with this query:
index=win_eventlogs | stats count by UserName
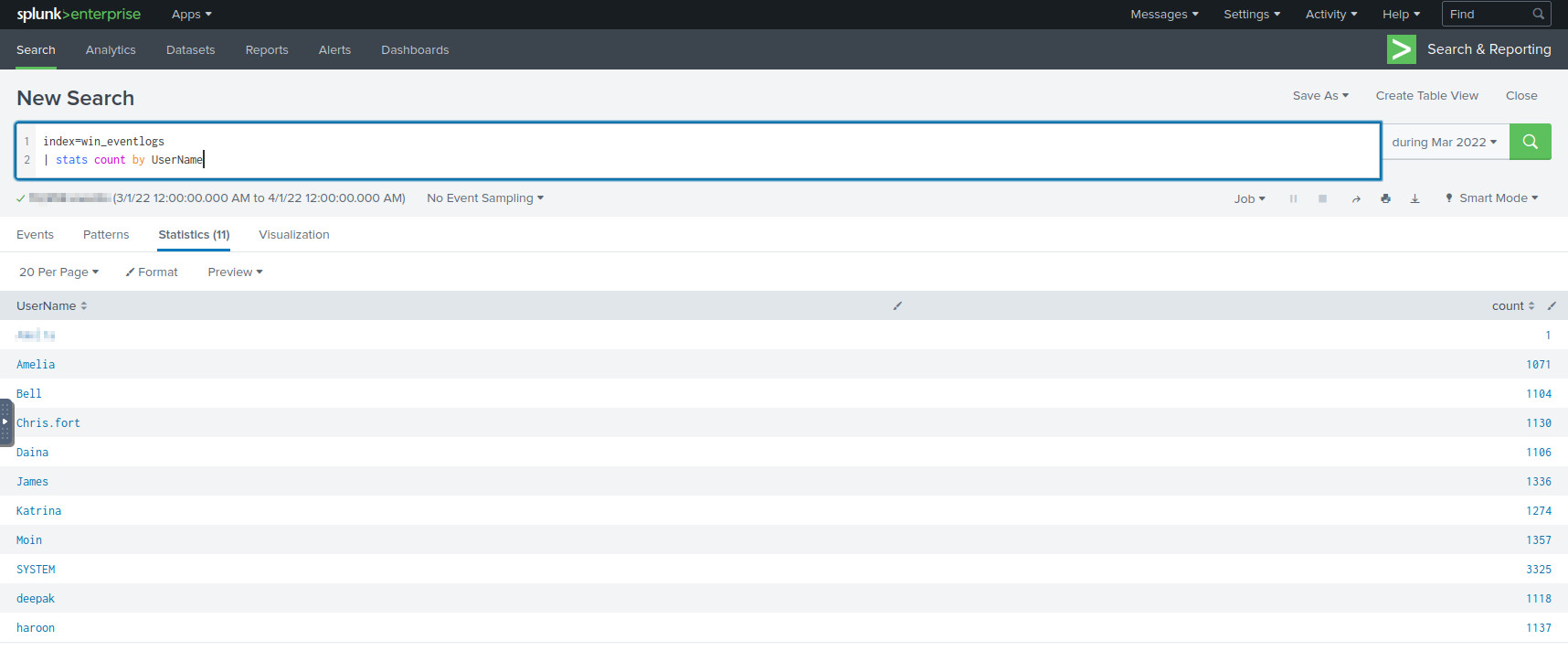
All the usernames detected.
There are 11 results, but we know that there’s only 9 real employees + 1 SYSTEM account. Look closely at the names, and the imposter will stick out like a sore thumb.
Which user from the HR department was observed to be running scheduled tasks?#
Let’s query the index again, but limit the search to only the users from the
HR department, and look for schtasks. schtasks.exe is the Windows process
for managing scheduled tasks:
index=win_eventlogs AND (UserName="haroon" OR UserName="Daina" OR UserName="Chris.fort") schtasks
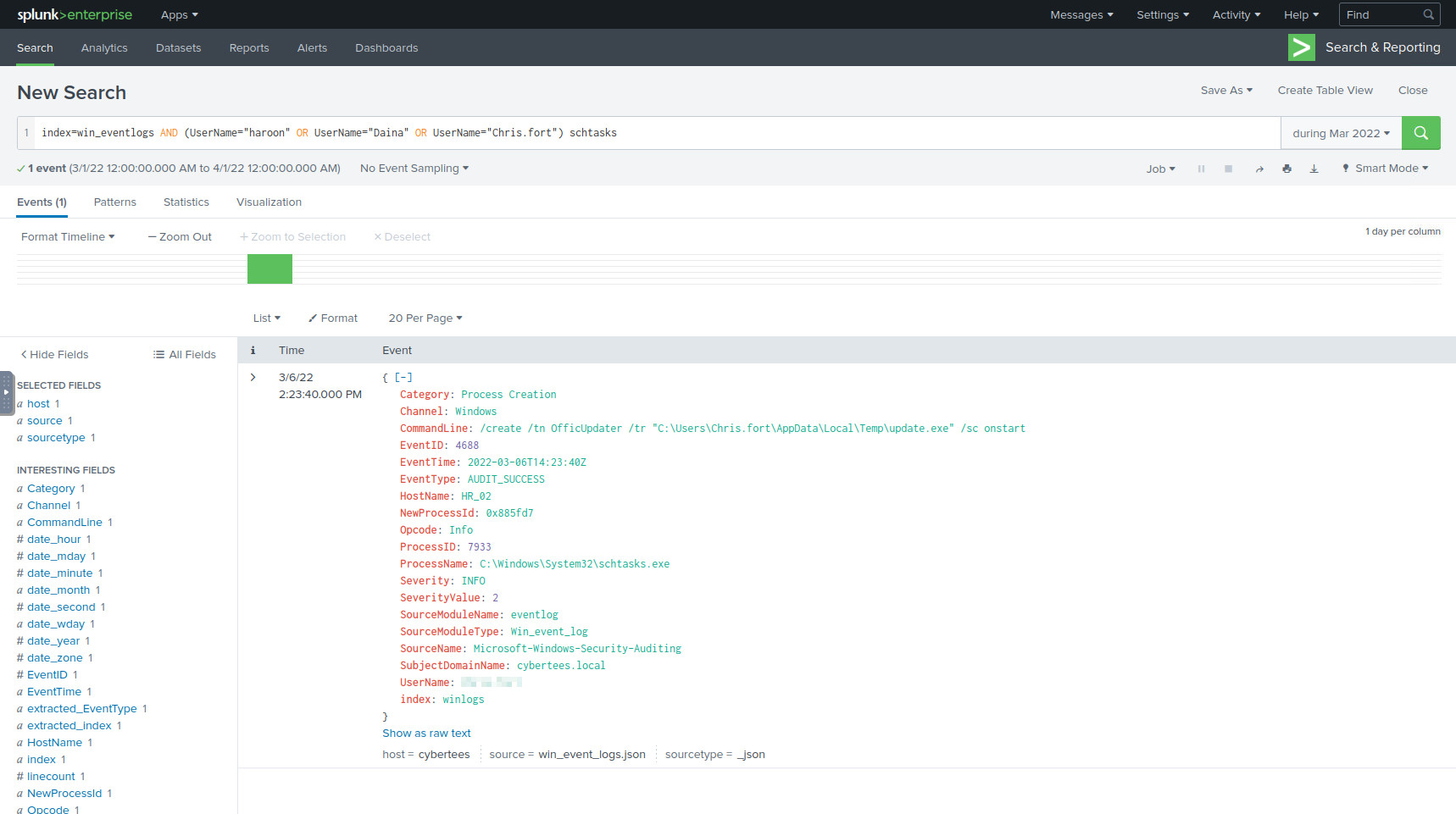
The scheduled task process in Splunk.
There’s only one result, so we have our answer.
Which user from the HR department executed a system process (LOLBIN) to download a payload from a file-sharing host?#
Let’s once again query the users from HR, but also create a table
containing the UserName, ProcessName, and CommandLine fields. We
should examine these fields closely because we know the user executed a system
process, and that would show up in the logs:
1index=win_eventlogs AND (UserName="haroon" OR UserName="Daina" OR UserName="Chris.fort")
2| table UserName ProcessName CommandLine
3| dedup UserName CommandLine
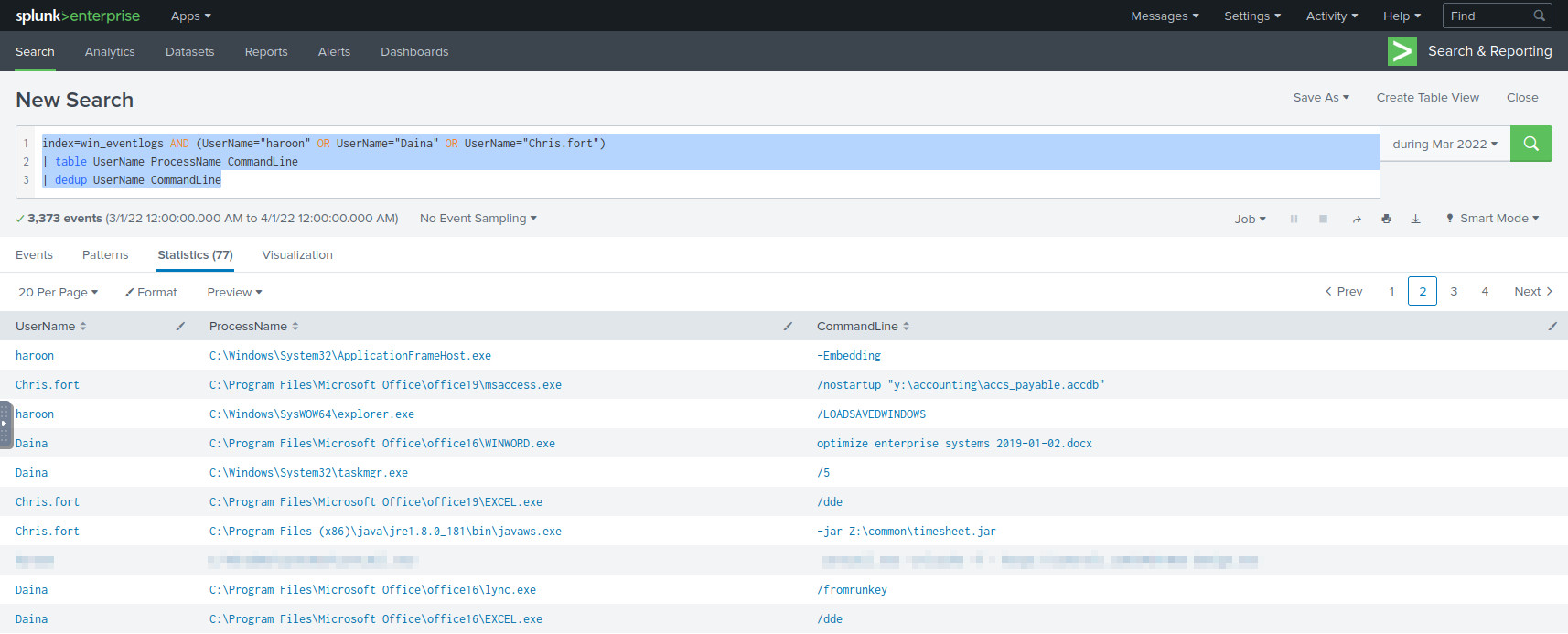
The system processes started by the HR users.
Sifting through the table, we can figure out which user downloaded the payload, what command they used, and the URL they downloaded it from.
To bypass the security controls, which system process (lolbin) was used to download a payload from the internet?#
This answer is also shown in the result from the previous question.
What was the date that this binary was executed by the infected host? format (YYYY-MM-DD)#
This answer is also shown in the result from Q4.
Which third-party site was accessed to download the malicious payload?#
This answer is also shown in the result from Q4.
What is the name of the file that was saved on the host machine from the C2 server during the post-exploitation phase?#
This answer is also shown in the result from Q4.
The suspicious file downloaded from the C2 server contained malicious content with the pattern THM{……….}; what is that pattern?#
This answer can be accessed by following the link in the result from Q4. I was initially hesitant to access the link myself, but after checking VirusTotal and other sources, I found out that this third-party site works like https://pastebin.com/. On this site, users can just share text documents publicly.
It’s completely benign, and we can can click on the link to view the text, which becomes the answer to this question.
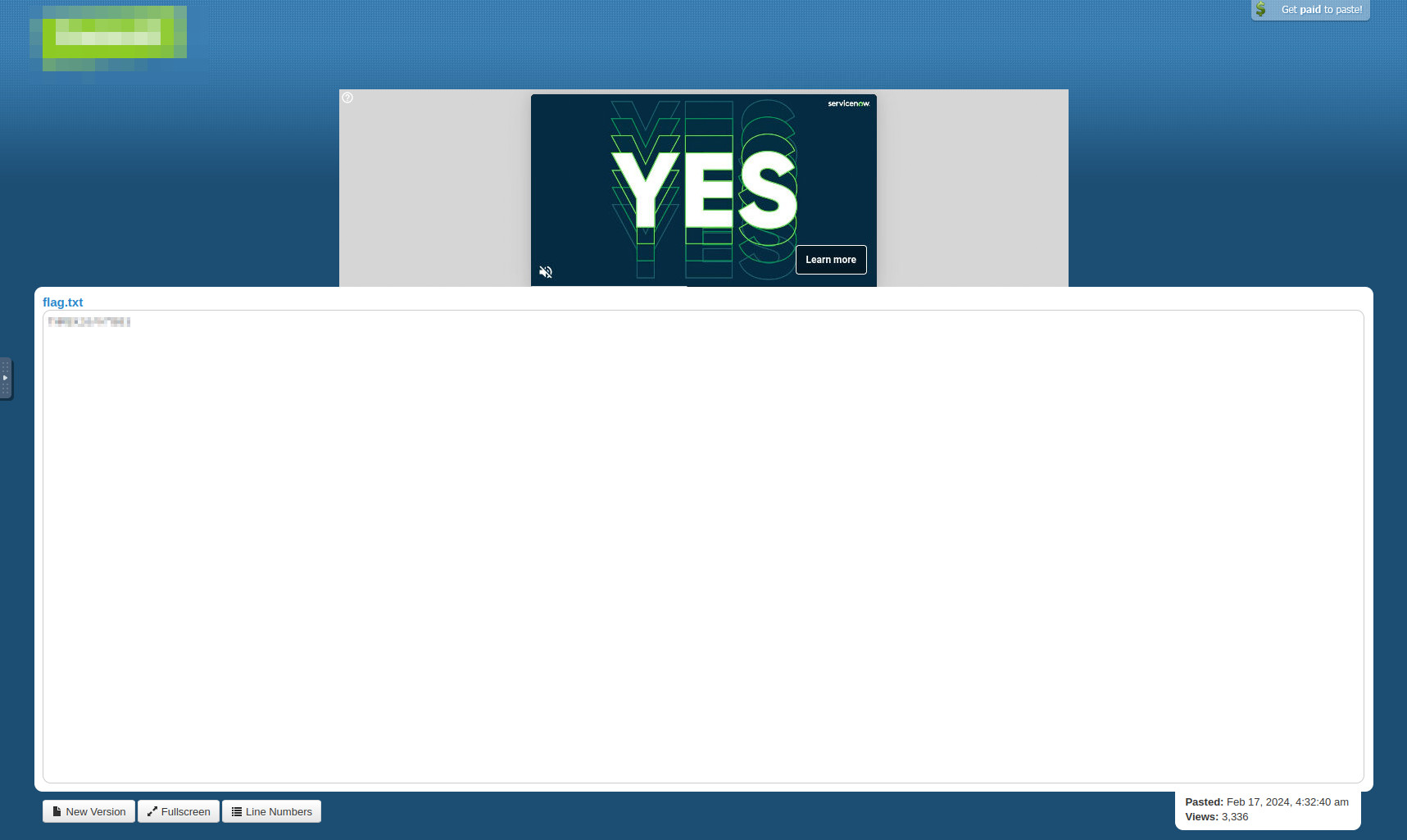
Result after clicking on the benign URL.
What is the URL that the infected host connected to?#
This answer is also shown in the result from Q4.
Conclusion#
And that’s it! Even though we only had access to a limited set of logs, we were still able to discover suspicious activity on the client’s system!
