This CTF is part of the Malware Analysis module on THM. In this scenario, you are tasked to analyze unknown malware samples detected by your Security Operations team.
You can find the link to Malbuster here: https://tryhackme.com/r/room/malbuster
This challenge covers static malware analysis, and provides two virtual machines to aid you in this task: A Windows-based FLARE VM, or a Linux-based REMnux VM. This guide will be written using the FLARE VM, but choose whichever suits you best. And the answers won’t be hidden this time!
Questions#
Based on the ARCHITECTURE of the binary, is malbuster_1 a 32-bit or a 64-bit application? (32-bit/64-bit)#
Open malbuster_1 in PEStudio, then select the file-header section. The
answer is given by the processor-32bit field, which is true.
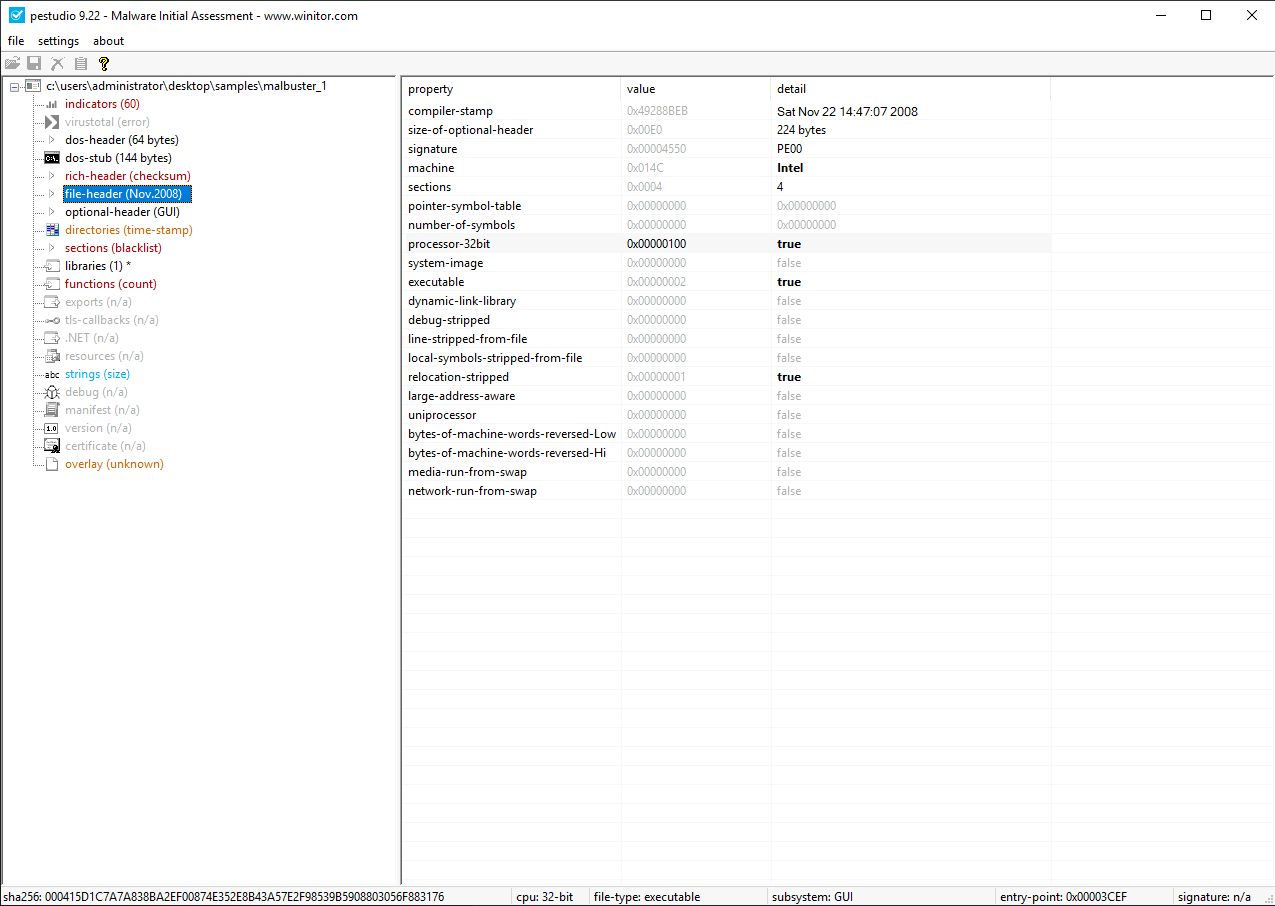
Answer: 32-bit
What is the MD5 hash of malbuster_1?#
There’s multiple ways to do this. You can simply run md5sum.exe from the
command line, or just check it in PEStudio by clicking on the top-most
section, the file name.
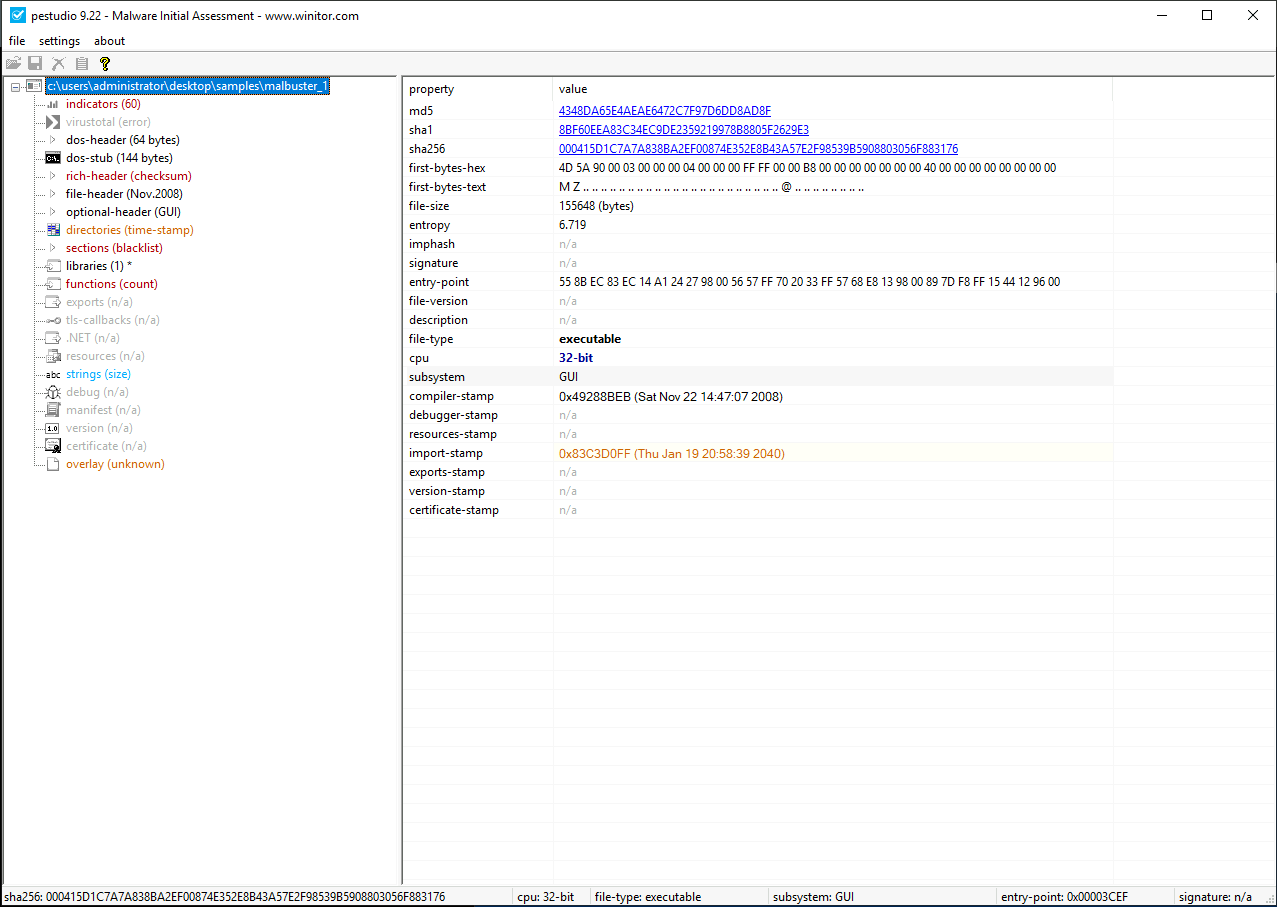
Answer: 4348DA65E4AEAE6472C7F97D6DD8AD8F
Using the hash, what is the number of detections of malbuster_1 in VirusTotal?#
Upload the hash to VirusTotal, and as of this writing, there are 60 detections of this malware. Though when this room was made, there were only 58 detections, which is the expected answer.
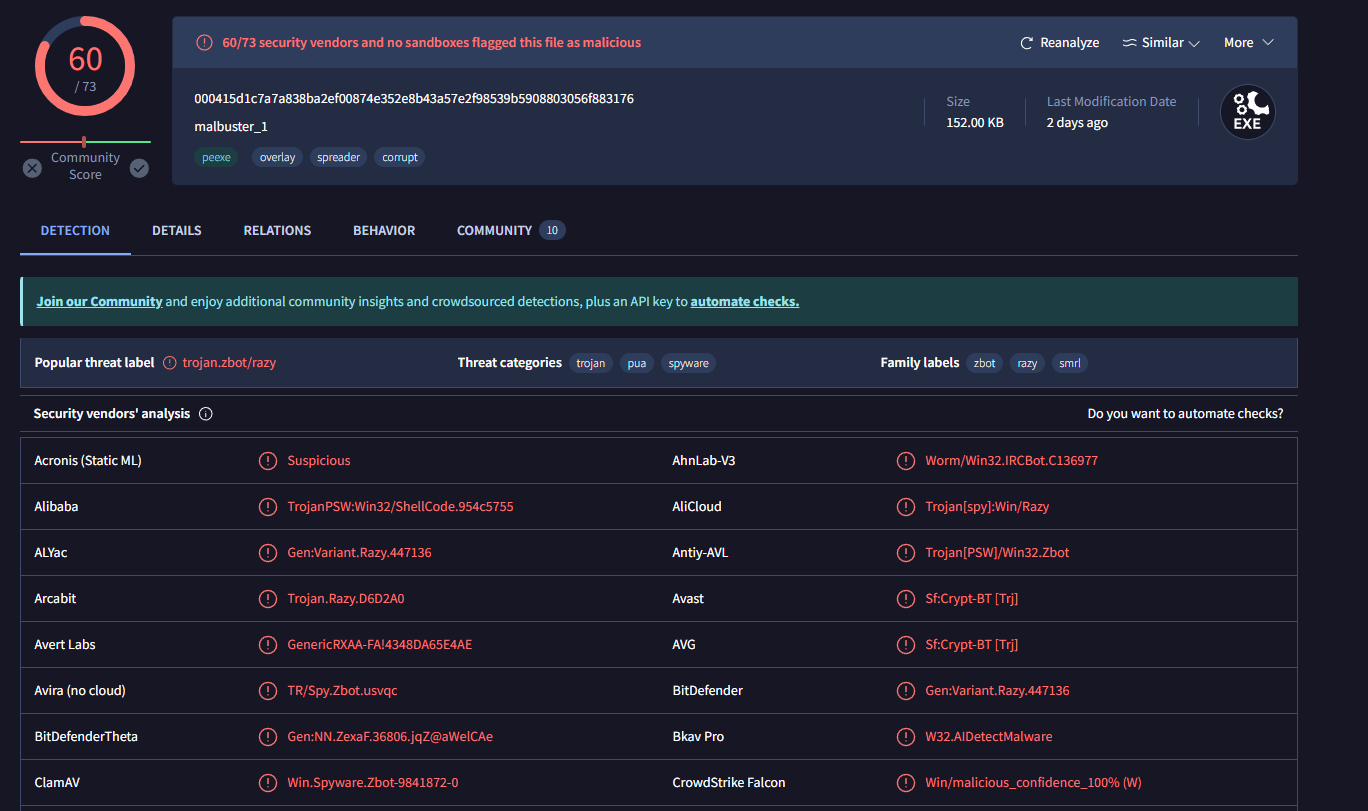
Answer: 58 (when the room was created)
Based on VirusTotal detection, what is the malware signature of malbuster_2 according to Avira?#
We can take a hash of malbuster_2, and check it on VirusTotal to view the
detections (ex. MD5, SHA256). Focus on the row with the detection from Avira,
and the second column is the signature.
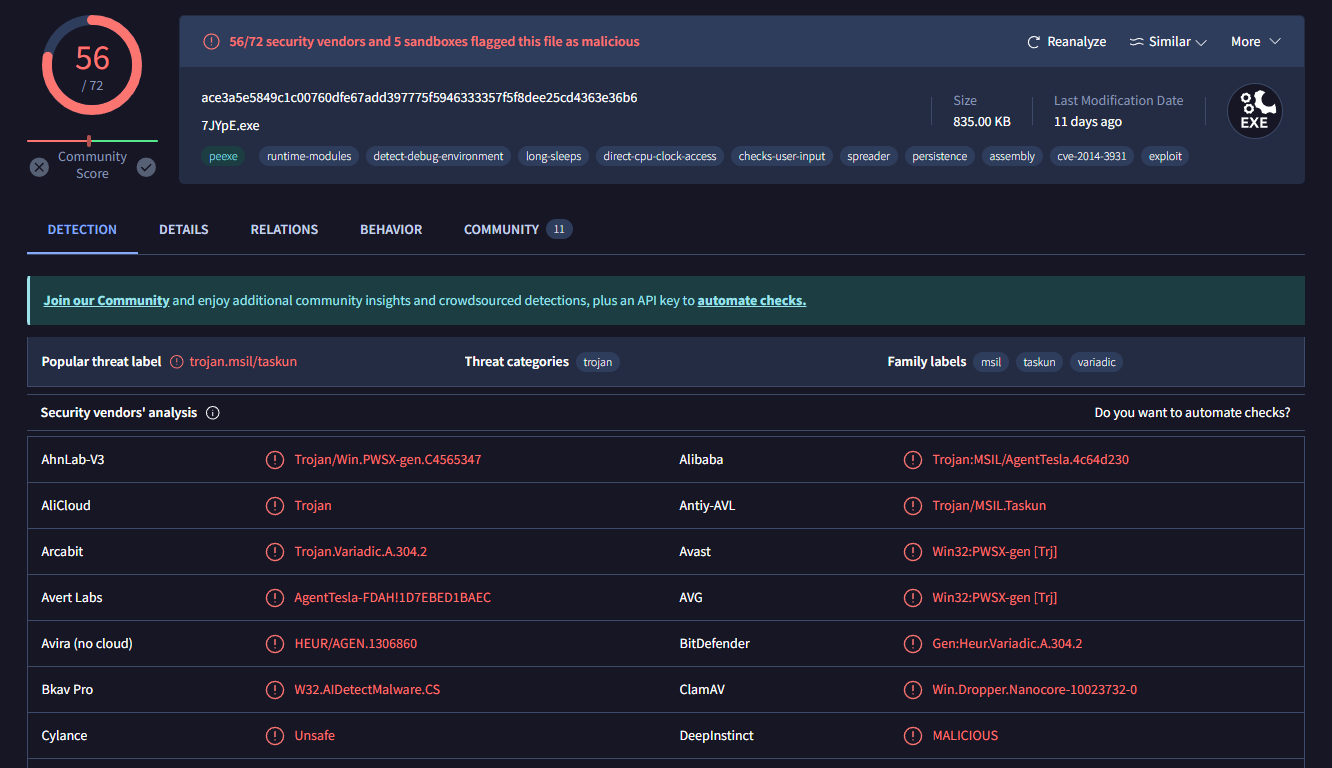
Answer: HEUR/AGEN.1306860
malbuster_2 imports the function _CorExeMain. From which DLL file does it import this function?#
Open the malware sample in PEStudio, and select the functions section. For
each function, it will also list the library that imports it, which is where
we’ll find the answer.
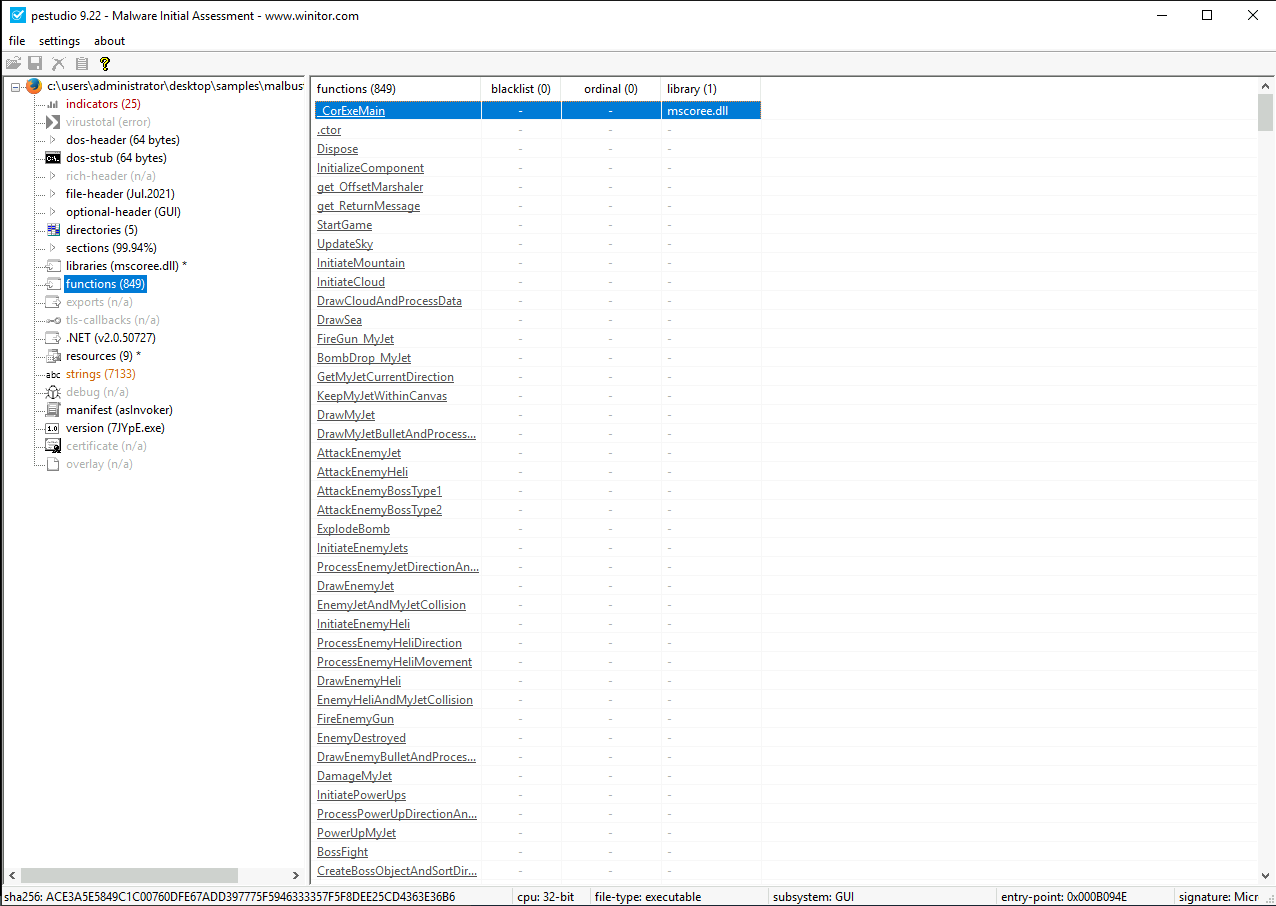
Answer: mscoree.dll
Based on the VS_VERSION_INFO header, what is the original name of malbuster_2?#
Still in PEStudio, select the version section, and the malware’s original
name is displayed in the OriginalFilename field.
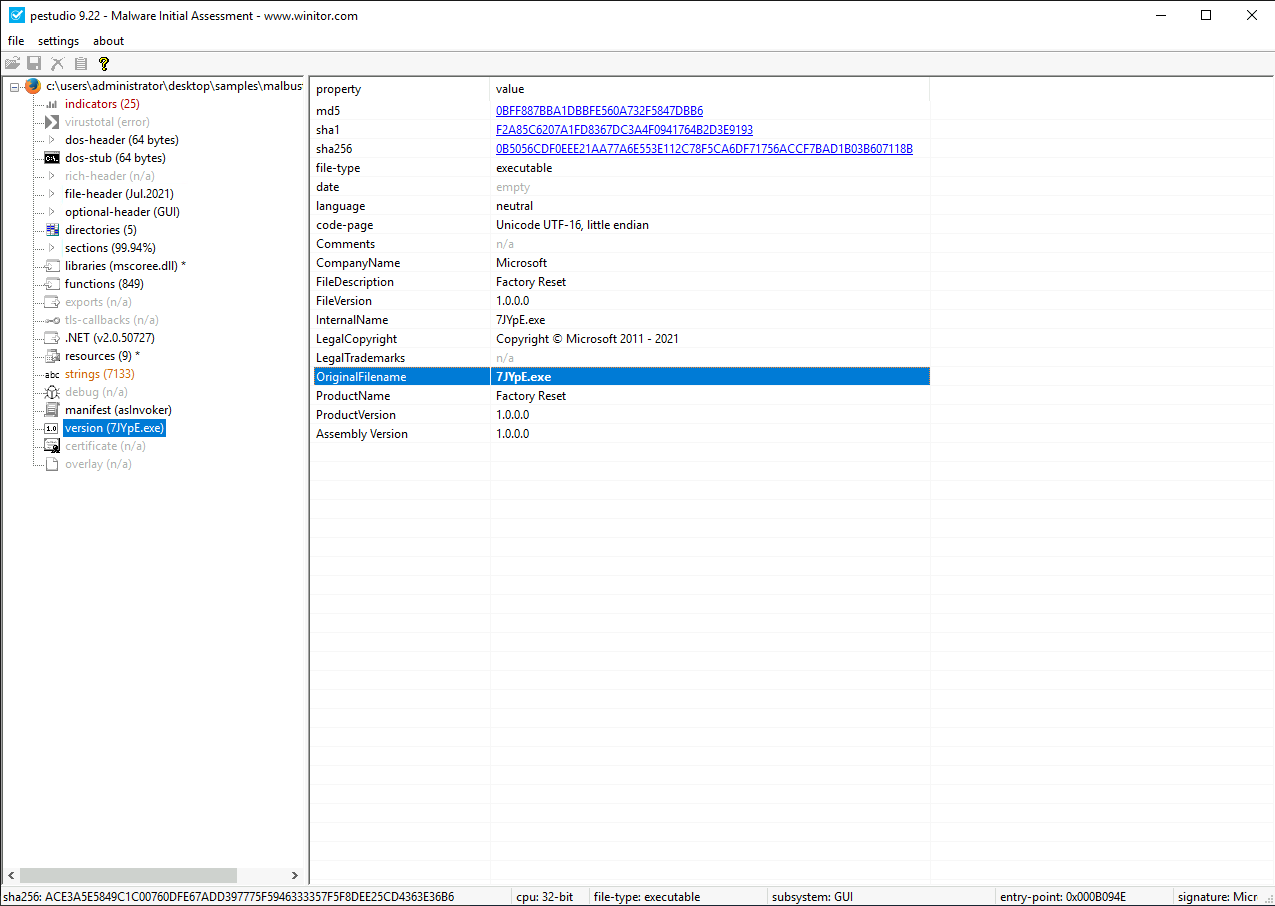
Answer: 7JYpE.exe
Using the hash of malbuster_3, what is its malware signature based on abuse.ch?#
Get the hash of malbuster_3, and search for it on abuse.ch. The answer will
be under the result’s Signature column.
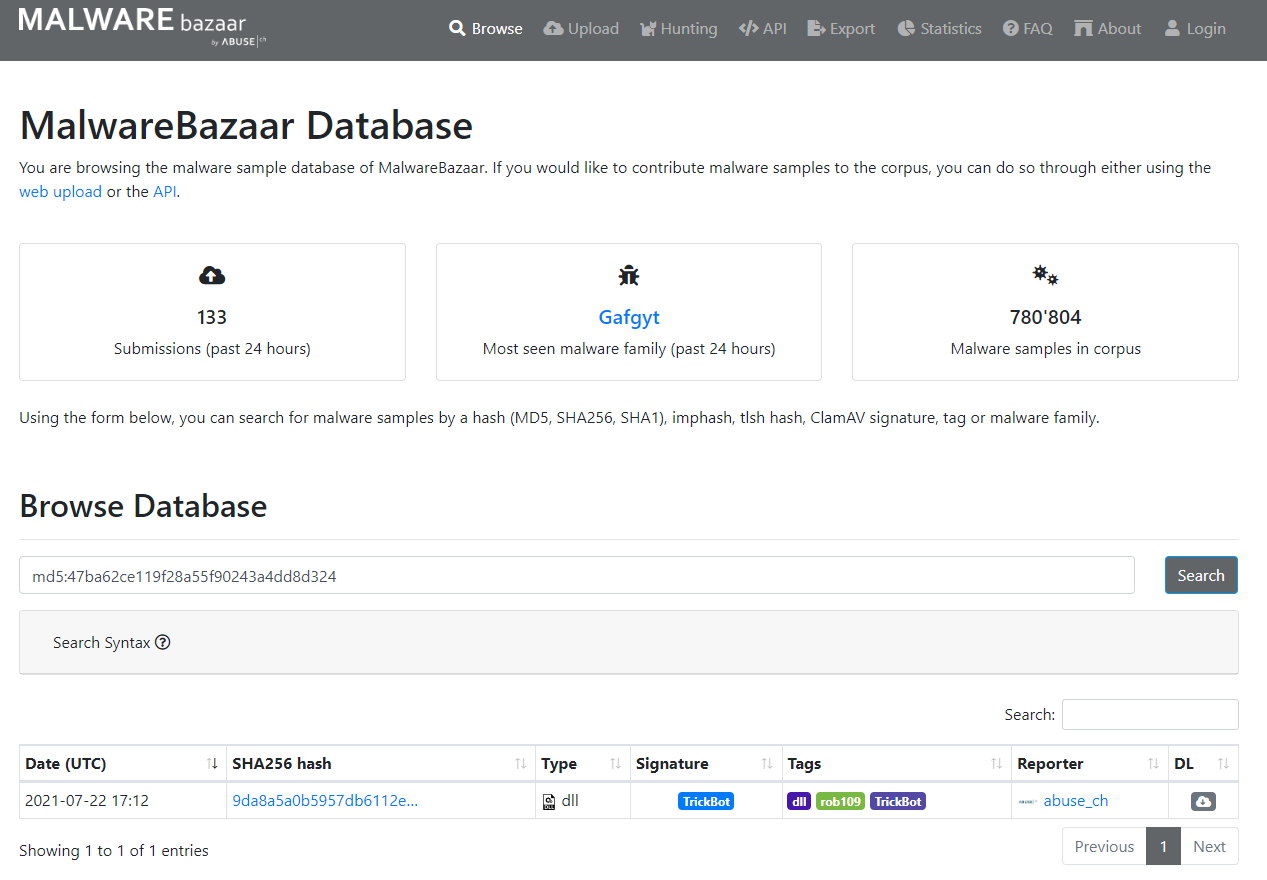
Answer: TrickBot
Using the hash of malbuster_4, what is its malware signature based on abuse.ch?#
Get the hash of malbuster_4, and search for it on abuse.ch. The answer will
be under the result’s Signature column.
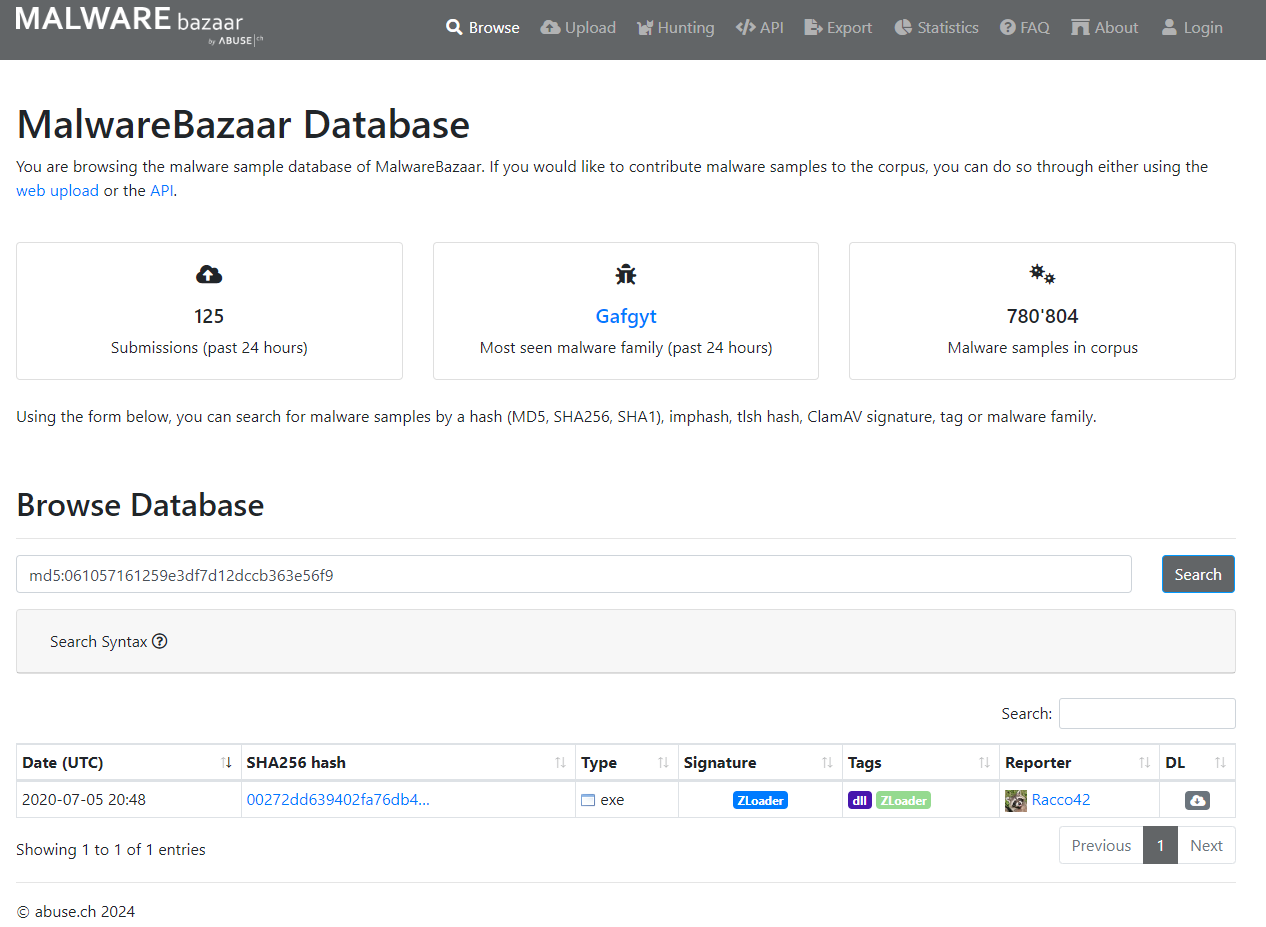
Answer: ZLoader
What is the message found in the DOS_STUB of malbuster_4?#
This one is a bit tricky. Open the sample in PEStudio, and when clicking
on the dos-stub section, there doesn’t seem to be any message. Go to the
strings section, and sort them by file-offset, because we know that the
DOS_STUB should appear as the earliest string.
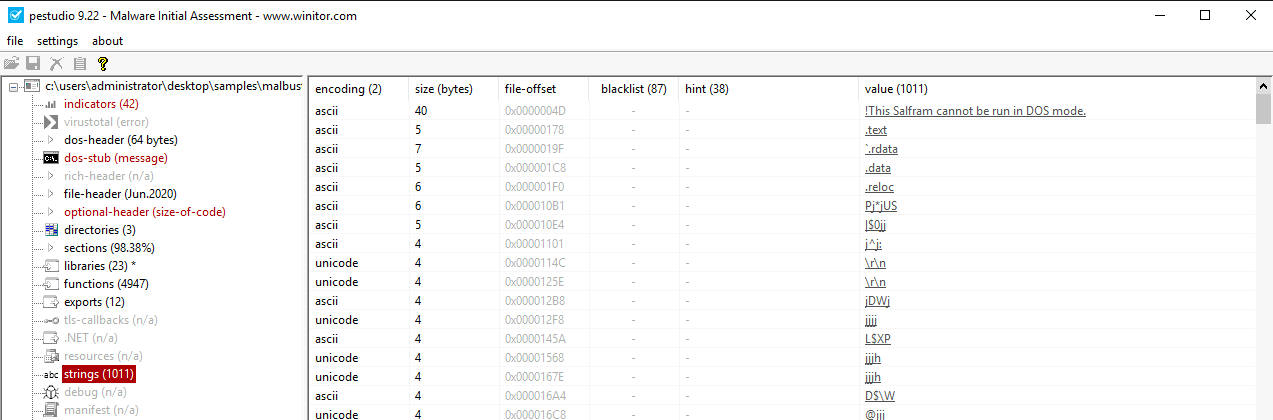
Answer: !This Salfram cannot be run in DOS mode.
Note: At this point we should realize that it’s highly likely that the malware has been packed in some way to obfuscate the data, making it harder to analyze.
malbuster_4 imports the function ShellExecuteA. From which DLL file does it import this function?#
In PEStudio, you’ll have trouble finding the DLL that imports this
function because it has been packed. Still, we can look at Microsoft’s
official documentation to find the library where the function ShellExecuteA
comes from.
According to MSDN, ShellExecuteA is imported with the shellapi.h header:
After doing some research on this header, there are only two DLL candidates,
and Shell32.dll is applicable for this malware:
Answer: Shell32.dll
Using capa, how many anti-VM instructions were identified in malbuster_1?#
Run capa against malbuster_1:
> capa.exe .\Desktop\Samples\malbuster_1
The answer is shown directly in the CAPABILITY table:
Answer: 3
Using capa, which binary can log keystrokes?#
Run capa against each of the binaries, and only one will have this capability
to log keystrokes.
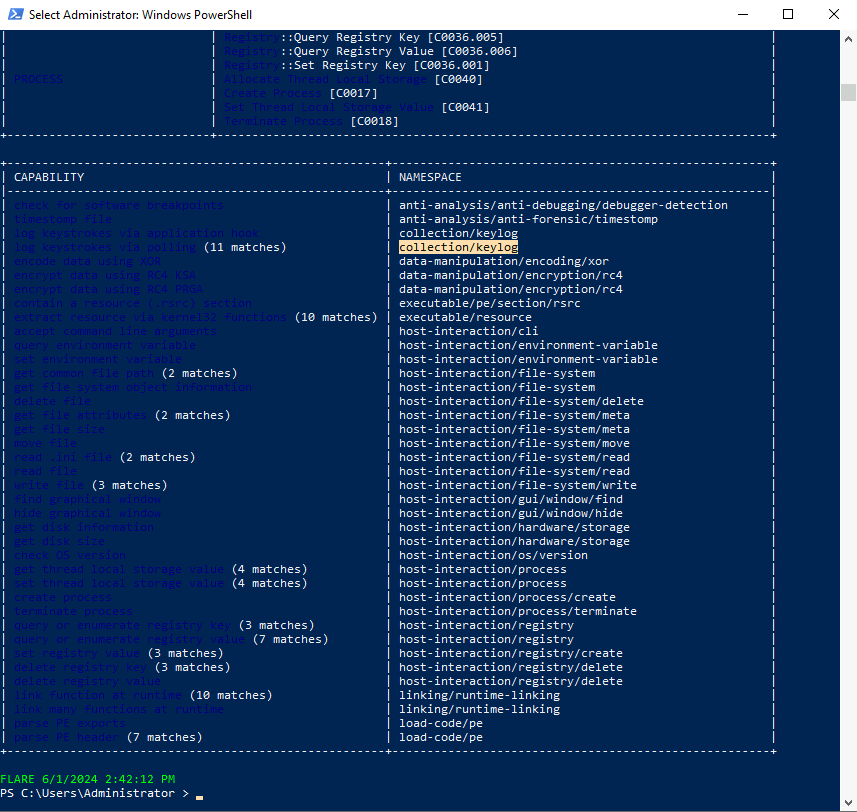
Answer: malbuster_3
Using capa, what is the MITRE ID of the DISCOVERY technique used by malbuster_4?#
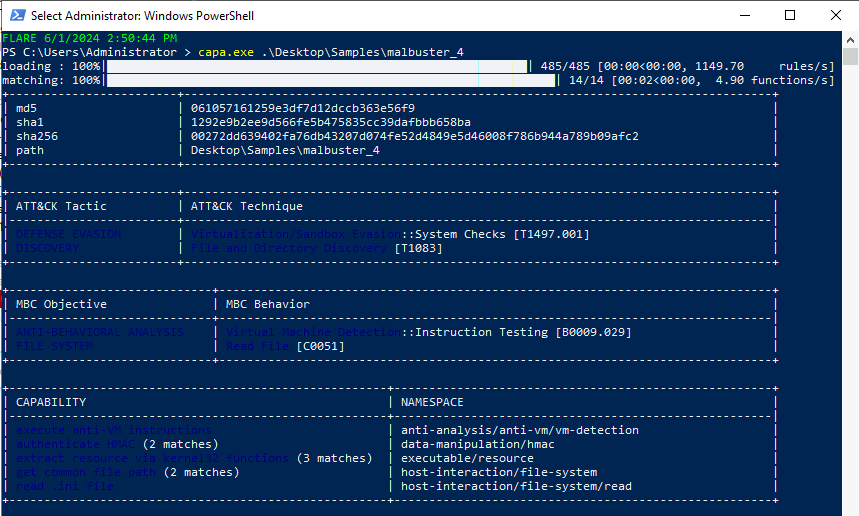
Answer: T1083
Which binary contains the string GodMode?#
Run strings.exe against each of the binaries, and we can use Select-String
to filter out results that have GodMode. There’s only one binary that should
yield results.
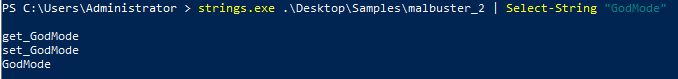
Answer: malbuster_2
Which binary contains the string Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)?#
Run strings.exe against each of the binaries, and we can use Select-String
to filter out results that have Mozilla/4.0. There’s only one binary that should
yield results.
Answer: malbuster_1
Conclusion#
And we’re done! This was a pretty simple room, but it shows just how much information we can glean from a malware sample without ever having to run it ourselves.
